Welcome back to LSB and thanks for reading. Today we will be looking at how to search for vulnerable devices around the world using Shodan.
Shodan is an index of all the devices in the world that are attached to the internet. It can be used to find all sorts of interesting things. From webcams to boats, we will show you how to find them.
To understand how Shodan works, we need to understand how any search engine works. Google, Yahoo or DuckDuckGo will spider websites and present the contents to you on a webpage, Shodan is a little different.
Instead of looking for websites, Shodan searches for every available port on the internet. So it is going around searching for every possible IP address and every possible port address trying to identify whether it is open and available. So it can recognize all the different devices connected to the internet.
While your home laptop probably won’t get indexed, your router probably will, and if you port forwarded anything from your home network, such as a webcam, that would probably show up in the search too.
You can find a vast array of devices on the internet, and what’s scary about it is that most of these devices still use the default password for that device.
What’s also great about Shodan is that it not only has a web interface that you may be familiar with, but it also has a command line module. We will be taking a look at both for this blog post.
All you will need for this tutorial is a browser and a command line interface.
Shodan has been revolutionary for security researchers because it allows you to search for very specific types of devices and find them all over the globe. So if there’s a zero day vulnerability that comes out to a certain type of hardware, Shodan allows us to search by make and model.
As always, this post is for educational purposes and should not be used on your friends or enemies, that’s illegal.
Also, the best way to search on Shodan is over a VPN or to use TOR, you don’t want to leave your IP on logs all over the world.
So head over to Shodan here.
Here is an interesting device we found through the search engine earlier.

What is interesting about this device?
As we can see on the map, it’s in a river, but a little more digging and we notice that it’s a satellite device that’s connected to a boat.
So how did we find a boat?
In the search bar in Shodan we can type vsat and this presents us with a list of satellite systems that have a login page or configuration with vsat in it.

We could also include in the search a port number, to whittle down the amount of devices we find.
So type vsat port:80. This allows us to search for a webcam or something that’s easy to access.
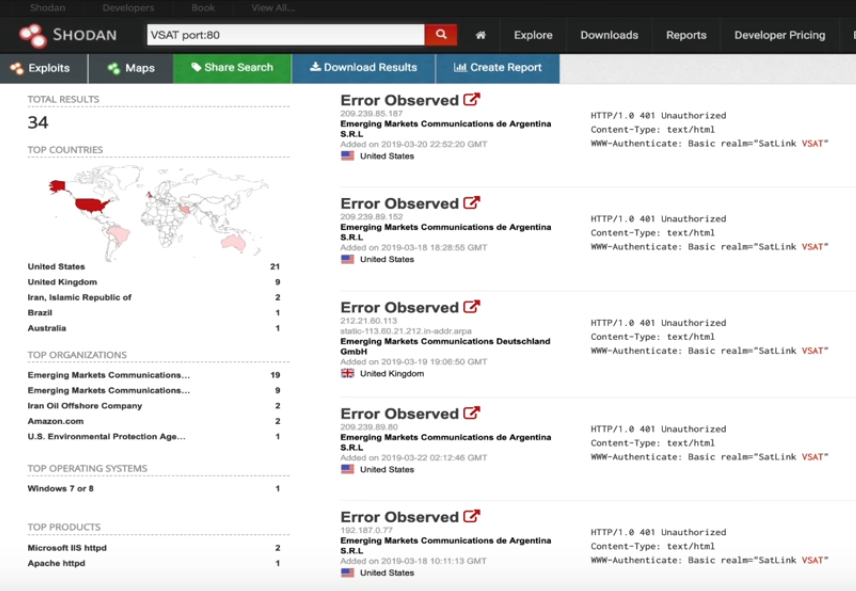
As we can see there is a lot of devices with SatLink in the description, this is really interesting. We could possibly get into a device that’s satellite connected and move us all over the world.
So let’s get back on the device we had earlier and we can see that ports 23, 80 and 161 are open.

To go to the device on the internet we just need to grab the IP and go to it in our browser.

This will bring us to the web interface of the device. Remember to only visit over a VPN or TOR browser.
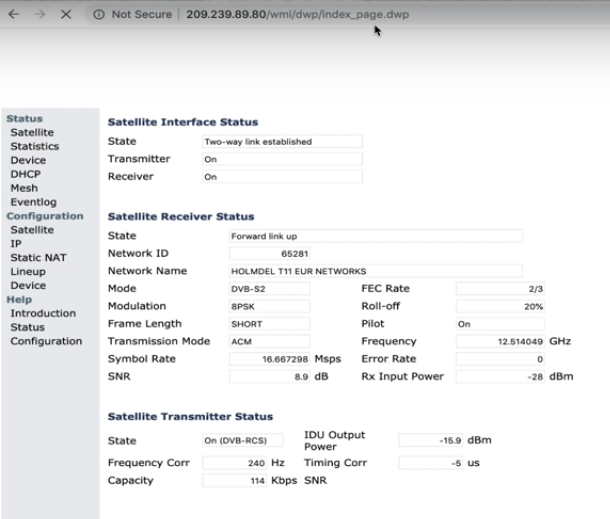
Most devices you find on the internet you will have to provide login details to get access. But with our sample above there was no authorization needed, we just got straight in. We seem to have accessed some kind of satellite network 🙂
Let’s have a dig around then. First off, when we click on the Lineup link at the side of the webpage we can see an upload link, so we could possibly upload some firmware.
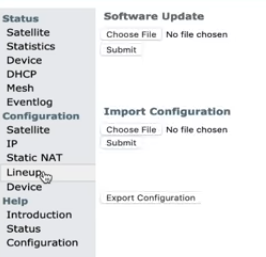
This means we could possibly make it a zombie. But we will not get into that in this post. We could also possibly route traffic through the device from the DHCP link on the side.

If you do get a login page for any of your searches, you can easily find the default logins online for the device and try to access it that way.
Let’s say you find a webcam on the internet. Like this one for instance.
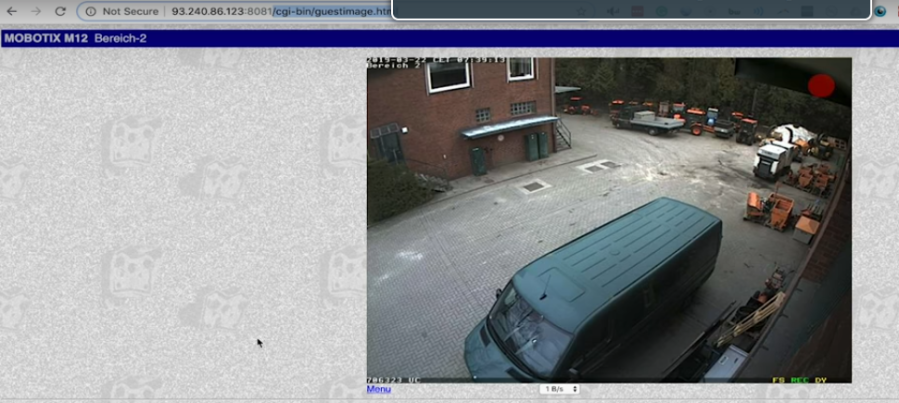
Above is a live webcam of somewhere in Germany, so let’s use Shodan to show us a few more webcams on different IP’s around the world. We just need to grab the name of the web page from the URL, /cgi-bin/guestimage.html, and enter that into Shodan’s search box.
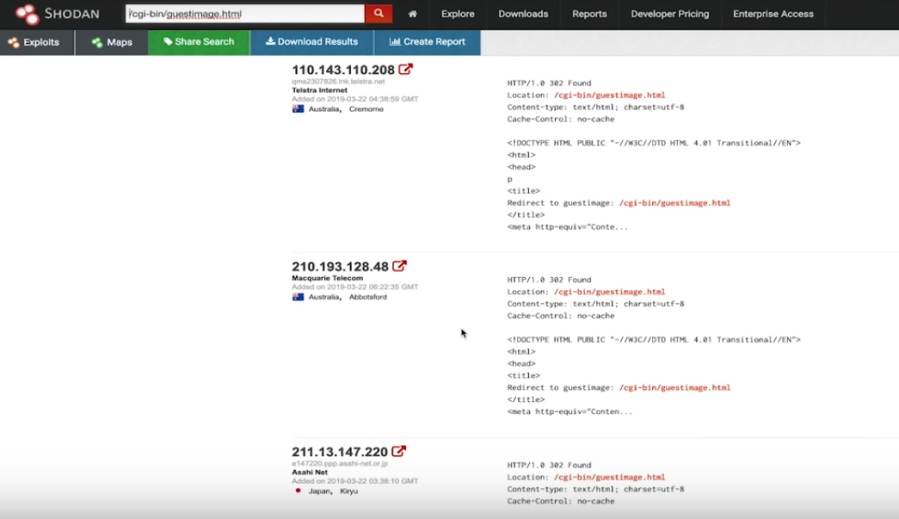
As we can see, this gives us a list of webcams around the world that we could possibly access.
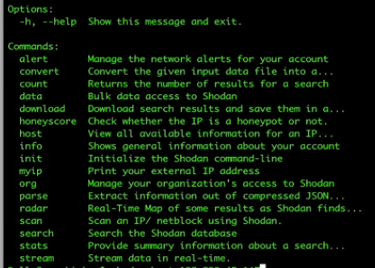
Next, let’s have a look at what we can do with Shodan on the command line interface. You will need to be logged in for the commands to work, so if you have not already done so, sign up to Shodan through their web page.
Also, if you Google shodan github, you will see the link for the Pythoon module.

To install the command line version of Shodan we type on the command line
pip install shodan
This will install all the appropriate libraries. Once that is installed we just need to type
shodan
and you’re good to go.
So now let’s query a host on the internet on the command line, type
shodan host 89.201.128.250
This will help us to distinguish if there are any vulnerabilities on the device.

This gives us a better idea of the device, like where it is and who owns it. From the details above we can see it’s in Mexico and it is vulnerable to the Heartbleed vulnerability. Interesting. Also, what ports are open and the type of device it is.
And that’s it, we hope you enjoyed this post and happy hunting!!
Please don’t forget to like or comment and please subscribe if you like the content.
Ciao for now!!
QuBits 2019-09-09

1 Comment