Valkyrie is a malware analysis tool that’s free for you for a year to try out. You can visit https://valkyrie.comodo.com to sign up.
Once you sign up you will presented with a dashboard with your stats for the site. So lets populate it. Let’s analyze a malware signature to see how it works.

First we need to grab a malware signature. Let’s move to our malware database and grab one of those bad boys.

Grab the file hash by adding it to your clipboard by clicking on the 3D square under FILE HASH. We then need to search for the fie hash on Valkyrie.

Valkyrie had a nice GUI and we can upload a file, analyze with a URL or in our case use a file hash. We have entered the file hash. So let’s see the results.
So there are several menus to choose from in the results so let’s go through the tabs one by one to get a better picture of what the malware is.

Summary Tab
Just a general overview of the file we are analyzing. The different hashes to the files. We can also see how many of our clients have been infected with the malware.
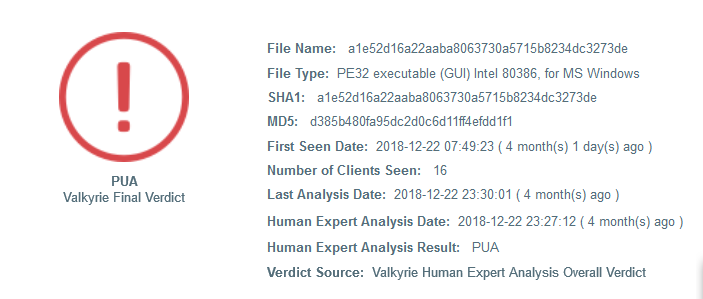
Underneath that we get a bit more information. This particular malware looks quite innocent but let’s dig down a bit further. We’ll move to the next tab.

Static Analysis Tab
Lots more information here on the fie we are analyzing. Here are the Valkyrie results.
| Static Analysis Overall Verdict | Result |
|---|---|
| No Threat Found | help |
| Detector | Result | |
|---|---|---|
| Optional Header LoaderFlags field is valued illegal | Clean | |
| Non-ascii or empty section names detected | Clean | |
| Illegal size of optional Header | Clean | |
| Packer detection on signature database | Unknown | help |
| Based on the sections entropy check! file is possibly packed | Clean | |
| Timestamp value suspicious | Clean | |
| Header Checksum is zero! | Clean | |
| Enrty point is outside the 1st(.code) section! Binary is possibly packed | Clean | |
| Optional Header NumberOfRvaAndSizes field is valued illegal | Clean | |
| Anti-vm present | Clean | |
| The Size Of Raw data is valued illegal! Binary might crash your disassembler/debugger | Suspicious | |
| TLS callback functions array detected | Clean | |
This gives us a bit more confidence to contact the customer and advise them to run a virus scan on the device and if they are unaware of the file, delete it. Thankfully this threat does not seem too dangerous.
Let’s move to the next tab for more information.
Precise Detectors Analysis Results
| Detector Name | Date | Verdict | Reason | |
|---|---|---|---|---|
| Static Precise PUA Detector 1 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise Trojan Detector 5 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise Trojan Detector 7 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise PUA Detector 4 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise PUA Detector 5 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise Trojan Detector 1 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise Trojan Detector 2 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise Trojan Detector 3 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise Trojan Detector 12 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise Trojan Detector 10 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise Virus Detector 1 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
| Static Precise Virus Detector 2 | 2018-12-22 07:48:29 | No Match | help | NotDetected |
A bit more confidence now to let the customer know that no infection has occurred on their device.
We will keep an eye out for some malware that’s extremely bad and do a further post on that analysis, which will probably be a bit more interesting.
We were just previewing Valkyrie for this post for those that have not used it yet. Hopefully you still enjoyed it. Leave us a comment below.
Ciao for now.
QuBits 2019-04-22
