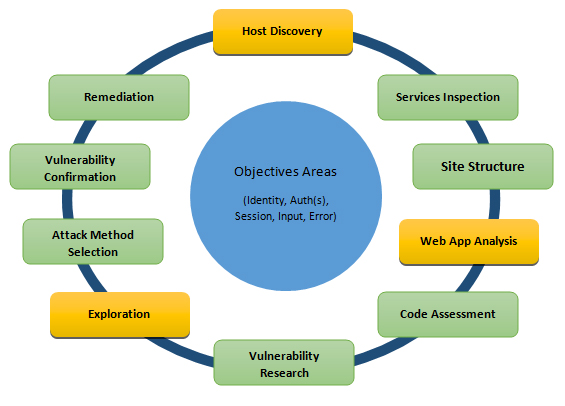
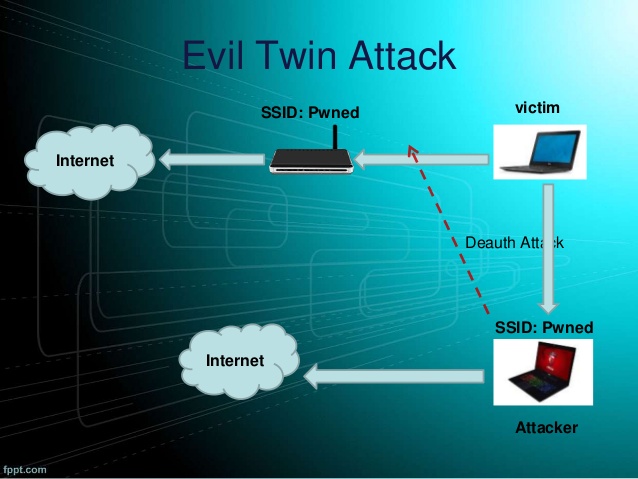
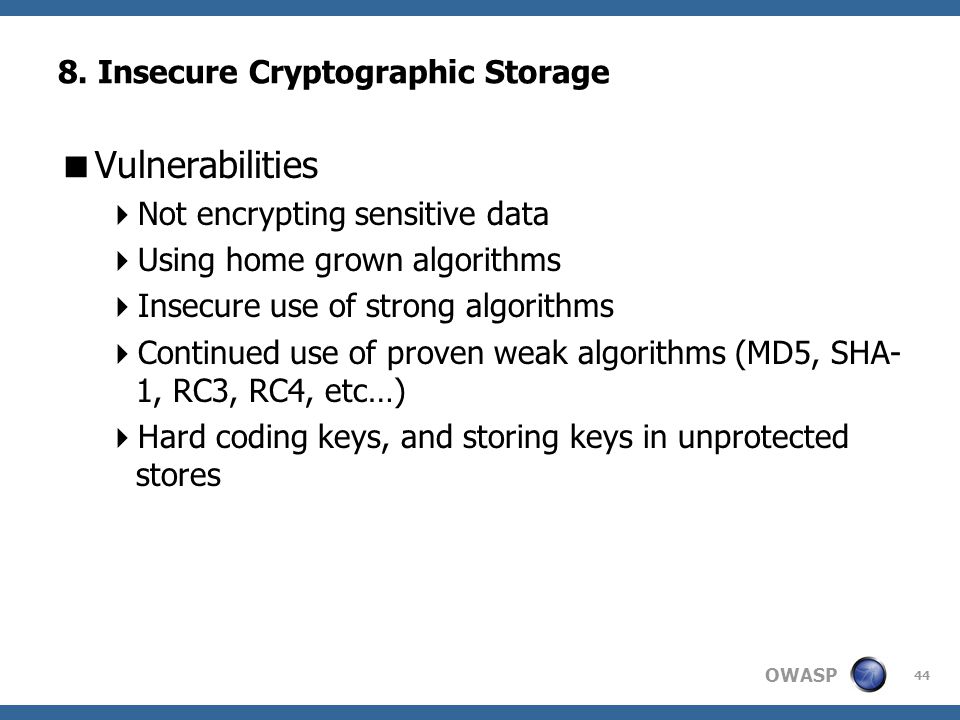
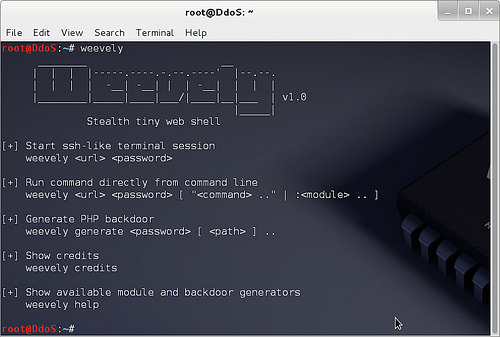
Category: Linux
-
 #career, #Metasploit, AI, Android, Android Security, AppSec, Attacks, Biometrics, Bugs, Cloud Security, Conferences, Crypto Currency, Cryptography, Cyber Security, Dark Net, Data Mining, Deals, Distros, Education, Encryption, Entertainment, Exploits, Firewalls, Hacking, Legal, Linux, Malware, Mobile Security, Open Source, Operating Systems, OWASP, Penetration Testing, Privacy, Security, SQL Injection, Technology, Tips, Tutorials, Virtual Machines
#career, #Metasploit, AI, Android, Android Security, AppSec, Attacks, Biometrics, Bugs, Cloud Security, Conferences, Crypto Currency, Cryptography, Cyber Security, Dark Net, Data Mining, Deals, Distros, Education, Encryption, Entertainment, Exploits, Firewalls, Hacking, Legal, Linux, Malware, Mobile Security, Open Source, Operating Systems, OWASP, Penetration Testing, Privacy, Security, SQL Injection, Technology, Tips, Tutorials, Virtual MachinesNow Is The Time, Linux is the Direction
-
 #career, #Metasploit, AppSec, Cloud Security, Cryptography, Cyber Security, Deals, Distros, Education, Entertainment, Exploits, Firewalls, Hacking, Linux, Open Source, Operating Systems, OWASP, Penetration Testing, Security, Technology, Tips, Tutorials, Virtual Machines
#career, #Metasploit, AppSec, Cloud Security, Cryptography, Cyber Security, Deals, Distros, Education, Entertainment, Exploits, Firewalls, Hacking, Linux, Open Source, Operating Systems, OWASP, Penetration Testing, Security, Technology, Tips, Tutorials, Virtual MachinesLinux Foundation Deals For LSB Followers