Originally the concept of an anonymous network, developed by the military, was to send and receive messages that were encrypted and hard to decipher.
Nowadays this network, known as the darknet network is used by a whole range of people, parties and organisations that, for whatever reason, want to remain anonymous.
The I2P network is made up of routers known as nodes with many multidirectional inbound and outbound paths. I2P refers to the connection between nodes as tunnels. The nodes use the same existing protocols we use for normal internet browsing for transport on the network.
Each node has a cryptic identifier that allows it to send and receive messages. Any client can connect to any router on the network and use different tunnels to send and receive messages. In other words, I2P is quite safe.
I2P is essentially a secure and anonymous communications mechanism that uses cryptographic keys to identify messages (messages are destinations), and the packets can be significantly larger than normal IP packets.
It is possible to configure your bandwidth with I2P. This enables larger file downloads than your internet service provider (ISP) might allow. To deal with online attacks I2P has no centralised resources and is fully distributed around the network. Therefore there are no servers checking the performance of the routers on the network.
Routers on the network store other random router information and are used to select the appropriate anonymity and reliability for users.
As well as this anonymity, the network is made up of a number of algorithms and cryptographic services.
One encryption type is ELGamal (2048bit) encryption.
ElGamal is used as an alternative to RSA encryption and is hugely difficult to decipher (2014, Leon). I2P also uses a mixture of 1024bit DSA signatures, 256bit AES, The Diffie-Hellman algorithm and SHA256, among others, for communication.
The operating system in use here is Linux Mint, so Debian, it might not work on other distros.
I2p darknet is quite complicated but the advantage it has over Tor is that it is quick.
So we are going to install I2P on our local server, then use our modem to forward traffic to the site once it’s done.
To install I2P on our server we must visit the I2P website (https://geti2p.net/en/download) and download the jar file for the install wizard.
There are several steps to take for installation and we will document these steps. Once the file is downloaded we simply click it twice to start the wizard. First we choose what language we would like the installer to speak to us in.
By selecting English we can then select OK. We are then informed about the installation and the version of I2P we will be using. The current distribution is 0.9.18. Click Next.
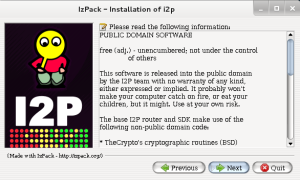
I2P next tells us that this is free software that can be modified and distributed by anyone and gives us some other random information about non-public domain code.
We can click next. The next step asks us where on our system I2P will store it’s files. This should be noted as we need to know where Honeyd is located and the directory it is ran from.
We can choose the default path that I2P has chosen for us or browse to place the files in
another directory if we like. For this exercise we will keep the default. Now I2P can be installed.
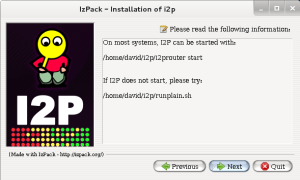
When the status bar confirms that the files have been installed we can then move to the next
step. I2P will tell us the commands to start up I2P router.
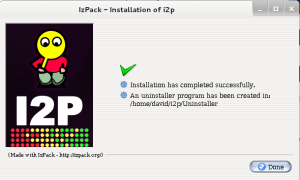
One final step, when we hit next, is for I2P to tell us we have successfully installed the
software.
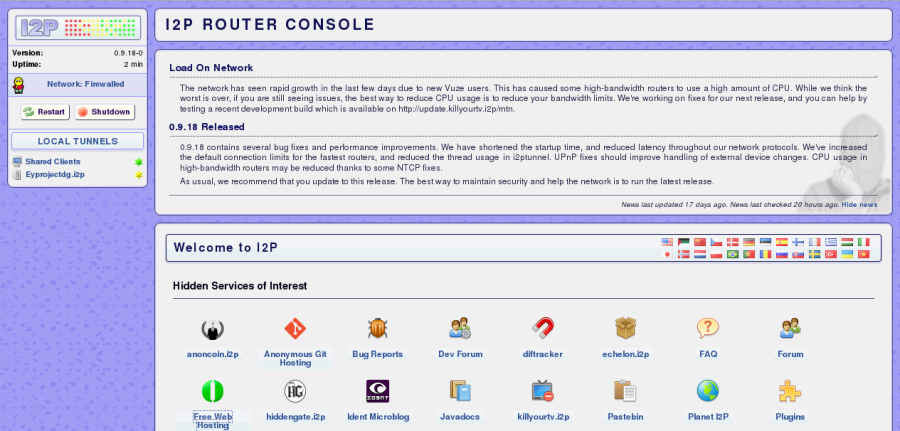
When installation is complete I2P opens up our router console on a web page automatically.
This webpage is stored locally at the address of 127.0.0.1/ console.
We won’t set up the router yet until the site is built and we can move to production.
Once the Darknet services have started we can set up some of what I2P offers, like encrypted email. Susimail is a fully encrypted end to end email service. I2p offers many different services and one could write a project on it alone. Another interesting service is I2P’s torrent service. With I2PSnark we have the capability to download any file we wish. Simply add the URL and click Add Torrent.
That completes the I2P installation and services. We can now set up the darknet website. For this task we will be using I2P’s fee hosting service to host our own darknet website. From the router console, choose the icon “Free Web Hosting”.
Everything we need to know about setting up our own Darknet website, step by step, is documented on the first page of the eepsite hosting service. Eepsite is the name of an I2P network hidden website.
The first step is to think of a name for the Darknet website. We chose the name eyprojectdg1.i2p. To accomplish this we must navigate to I2P’s Hidden Services Configuration Page and enter the details we want for the darknet website.
We enter the name we want for the name of our site in the Name field, add a description and tick the Auto Start checkbox for the website to start up when the server does.
All changes are made locally so in the Target field we want to specify port 7658. Note the Local Destination option also. This is the base64 string key for our Darknet site destination. Copy the whole thing and save it in the local addressbook page as we will need that in a later step.
It can take up to four days for the website to go live. I2P uses cryptic tunnels to set up communications between nodes. Before our website can be broadcast live, we first need to share our Base64 key to I2P for authorisation, and afterwards, set up an encrypted tunnel to enable communications.
The base64 Darknet local address that was placed in the local addressbook of I2P needs to be shared with stats.i2p , the darknet hosts, to set up a live darknet site.
All destinations in I2P are 516 byte key strings, the base64 address of our eepsite (Darknet site) is our key.
This is made up of a 256 byte public key, a 128 byte signing key and a null certificate. In Base64 this is 516 bytes. Eepsites, such as our Darknet site, use these keys as cryptic identifiers. To complete this task navigate to stats.i2p, fill out the details and you are done.
As mentioned it can take up to four days for the Darknet website to go live. We know the site is live when the peers begin to propogate on the network. This is shown in the I2P dashboard of the router console.
All you have to do now is give your site some content. This is done by navigating to /home/.i2p/eepsite/docroot and changing the contents of index.html, instead of the default page that I2p gives us.
Note the dot (.) before i2p in the directory. This is a hidden directory within the I2P file system..
Last thing to do is go to your router settings and port forward to the IP. This will send the outside world to that port after it hits your router.
localhost:7658
I hope you found this blog helpful, drop me a line and let us know what you think.












You should take part in a contest for one of the best blogs on the web. I will recommend this site!
LikeLike
Hi! I could have sworn I’ve been to this blog before but after browsing
through a few of the posts I realized it’s new to me. Regardless, I’m certainly pleased I stumbled upon it and I’ll be book-marking it and checking back
frequently!
LikeLike
Thanks for sharing your info. I really appreciate your efforts and I am waiting for your further write ups
thanks once again.
LikeLike
Thank you a lot for sharing this with all folks you actually recognise what you are speaking
about! Bookmarked. Kindly also visit my web site =).
We may have a hyperlink change arrangement between us
LikeLike
I want to to thank you for this excellent read!! I absolutely enjoyed every little bit of it.
I’ve got you bookmarked to look at new things you post…
LikeLike
Nice article..keep it up
LikeLike
Having read this I thought it was really informative. I appreciate you finding the time and effort to put this short article together.
I once again find myself personally spending way too much time both reading and commenting.
But so what, it was still worth it!
LikeLike
I like the valuable info you provide in your articles.
I will bookmark your blog and check again here regularly.
I am quite certain I will learn many new stuff right here!
Good luck for the next!
LikeLiked by 1 person
Try WordPress. There are many tutorials on Youtube. 🙂 Thanks for the comment.
LikeLike
Howdy great blog! Does running a blog similar to this require a
lot of work? I have virtually no expertise in computer
programming but I had been hoping to start my own blog soon. Anyhow, if you have any recommendations or tips
for new blog owners please share. I understand this is off topic however I just needed to ask.
Kudos!
LikeLike
And it works!
LikeLike